On 5G Service-Based Interface (SBI)
The 5G Service-Based Interface (SBI) serves as a foundational element within the architecture of 5G networks, facilitating communication and interaction between various network functions. As 5G networks are designed to be highly flexible, scalable, and efficient, the SBI plays a critical role in enabling seamless connectivity, dynamic service orchestration, and interoperability across diverse network elements. Let’s delve into a detailed introduction of the 5G Service-Based Interface:
-
Definition and Purpose: The 5G Service-Based Interface (SBI) is a standardized interface within the 5G architecture, defined by the 3rd Generation Partnership Project (3GPP). It establishes a set of protocols, procedures, and messaging formats for communication between different network functions, allowing them to exchange information, invoke services, and coordinate actions. The primary purpose of the SBI is to enable service-oriented architecture (SOA) principles within 5G networks, promoting modularity, flexibility, and reusability of network functions.
-
Service-Oriented Architecture (SOA): At the core of the 5G SBI is the concept of service-oriented architecture (SOA), which advocates for the decomposition of network functionality into discrete, interoperable services. By encapsulating network functions as services with well-defined interfaces, SOA enables greater agility, scalability, and composability within the network. The SBI embodies the principles of SOA by providing a standardized framework for service discovery, invocation, and composition, facilitating dynamic service provisioning and adaptation.
-
Interface Abstraction: The 5G SBI abstracts the underlying network infrastructure, allowing network functions to interact in a vendor-neutral and technology-agnostic manner. This abstraction layer shields higher-layer applications and services from the complexities of the underlying network, promoting interoperability and innovation. By adhering to standardized interface specifications, vendors and operators can develop and deploy network functions independently, fostering a vibrant ecosystem of interoperable solutions.
-
Protocol Stack: The 5G SBI is built upon a modern protocol stack, leveraging industry-standard protocols such as HTTP/2, RESTful APIs, and JSON (JavaScript Object Notation) for communication between network functions. These lightweight, web-friendly protocols enable efficient data exchange, asynchronous messaging, and stateless interactions, ideal for dynamic service orchestration and resource management in 5G networks. Additionally, the SBI may utilize protocols such as gRPC (gRPC Remote Procedure Calls) for high-performance, bi-directional communication between network functions.
-
Functional Components: Within the 5G SBI, various functional components play distinct roles in facilitating service discovery, invocation, and management. These components include Service Consumer, Service Provider, Service Registry, Service Gateway, and Service Orchestrator. The Service Consumer initiates service requests, while the Service Provider delivers the requested services. The Service Registry maintains a catalog of available services, while the Service Gateway serves as a proxy for routing and security. The Service Orchestrator coordinates the deployment and lifecycle management of services, ensuring optimal resource utilization and service quality.
-
Dynamic Service Orchestration: One of the key advantages of the 5G SBI is its support for dynamic service orchestration, allowing network functions to be instantiated, configured, and interconnected on-the-fly in response to changing demand and network conditions. Through automated service discovery, composition, and provisioning, the SBI enables efficient resource allocation, traffic optimization, and service chaining, maximizing the utilization of network resources and enhancing user experience.
For instance:
- Namf: SBI exposed by Access and Mobility Management Function (AMF)
- Nsmf: SBI exposed by Session Management Function (SMF)
- Nnef: SBI exposed by Network Exposure Function (NEF)
- Npcf: SBI exposed by Policy Control Function (PCF)
- Nudm: SBI exposed by Unified Data Management (UDM)
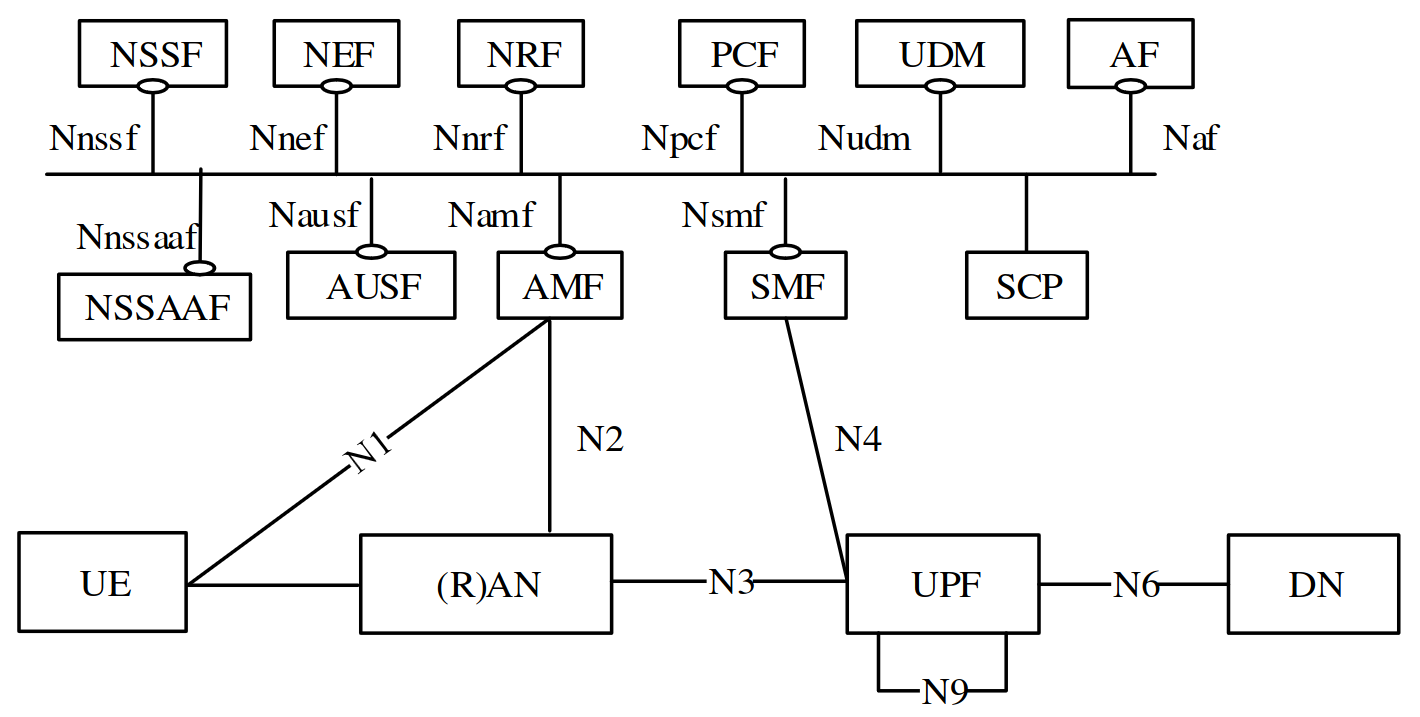
The registration of a User Equipment (UE) in a 5G network involves several steps, including authentication, authorization, and the establishment of a connection with the network’s core. Here’s a detailed overview of the registration procedure with a focus on the HTTP/2 messages involved:
-
Initial Access and Authentication Request: When a UE initially accesses the 5G network, it sends an initial registration request to the Access and Mobility Management Function (AMF), which acts as the control plane node for access management. This request is typically sent over a secure connection using HTTP/2, initiated by the UE’s User Plane Function (UPF). The HTTP/2 request contains information such as the UE’s identity (e.g., International Mobile Subscriber Identity or IMSI), capabilities, and location.
-
Authentication and Security Setup: Upon receiving the registration request, the AMF initiates the authentication process by requesting authentication vectors from the Authentication Server Function (AUSF). The AUSF responds with authentication vectors (RAND, AUTN) and authentication key (K) based on the UE’s identity. The AMF uses these authentication vectors and the stored security parameters to authenticate the UE and d erive session keys for secure communication. HTTP/2 messages exchanged during this phase typically include authentication request/response payloads, encrypted with security keys derived from the authentication process.
-
Registration Procedure: After successful authentication, the AMF proceeds with the registration procedure, assigning temporary identifiers and establishing a session context for the UE. The AMF may allocate resources and set up policies based on the UE’s profile and service requirements. HTTP/2 messages exchanged during this phase include registration request/response payloads, confirming the successful establishment of the session context.
-
Establishment of Data Path: Following registration, the AMF coordinates with the UPF to establish the data path for the UE, allowing data packets to be forwarded between the UE and external networks. This involves setting up tunnels, configuring QoS parameters, and applying traffic policies based on the UE’s subscription and network conditions. HTTP/2 messages exchanged between the AMF and UPF may include signaling messages to establish and manage data tunnels, update QoS settings, and handle mobility events.
-
Finalization and Confirmation: Once the data path is established, the AMF sends a confirmation message to the UE, indicating the successful registration and activation of services. The UE may also send acknowledgment messages to confirm the reception of configuration parameters and activation of services. HTTP/2 messages exchanged during this phase include confirmation/response payloads, signaling the completion of the registration process.
Throughout the registration procedure, HTTP/2 messages serve as the transport mechanism for exchanging control plane signaling between the AMF, and other network elements. These messages carry essential information for authentication, session establishment, resource allocation, and service activation, ensuring seamless connectivity and service delivery in the 5G network. In summary, the 5G Service-Based Interface (SBI) serves as a cornerstone of the 5G architecture, enabling modular, interoperable, and dynamic networking capabilities.